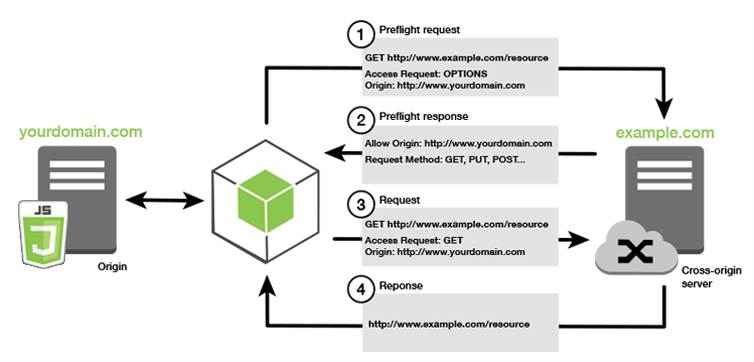
Cross-Origin Resource Sharing (CORS) is a security feature implemented by web browsers to control how resources are requested from a different origin than the one that served the web page. Understanding and handling CORS is essential for backend developers to enable secure cross-origin requests while maintaining application security.
What is CORS?
CORS defines a way in which a browser and server can interact to determine whether or not to allow the cross-origin request. By default, web applications are restricted by the same-origin policy, which prevents malicious scripts from accessing sensitive data on another site.
Key Concepts:
- Origin: Comprised of the scheme, host, and port of a URL.
- Same-Origin Policy (SOP): A security measure that restricts how documents or scripts from one origin can interact with resources from another origin.
- CORS Headers: HTTP headers that control CORS permissions, such as
Access-Control-Allow-Origin,Access-Control-Allow-Methods, andAccess-Control-Allow-Headers.
How CORS Works
When a web application makes a cross-origin HTTP request, the browser automatically adds an Origin header indicating the source of the request. The server responds with specific CORS headers to either allow or deny the request.
Simple Requests vs. Preflight Requests
- Simple Requests: Use methods like GET, HEAD, or POST with standard headers. They don’t trigger a preflight.
- Preflight Requests: Sent automatically by the browser before the actual request using the OPTIONS method to check if the server permits the actual request.
Example:
Client Request (with Origin Header):
GET /api/data HTTP/1.1
Host: api.example.com
Origin: http://client.example.comServer Response (with CORS Headers):
HTTP/1.1 200 OK
Access-Control-Allow-Origin: http://client.example.com
Access-Control-Allow-Methods: GET, POST
Access-Control-Allow-Headers: Content-TypeHandling CORS in Backend Development
1. Setting CORS Headers
- Access-Control-Allow-Origin: Specifies the allowed origin(s).
- Access-Control-Allow-Methods: Lists permitted HTTP methods.
- Access-Control-Allow-Headers: Specifies allowed request headers.
2. Implementing CORS in Different Backend Technologies
Node.js (Express):
const express = require('express');
const cors = require('cors');
const app = express();
app.use(cors()); // Enable CORS for all routes
app.get('/api/data', (req, res) => {
res.json({ message: 'CORS-enabled for all origins!' });
});
app.listen(3000, () => console.log('Server running on port 3000'));Python (Flask):
from flask import Flask
from flask_cors import CORS
app = Flask(__name__)
CORS(app) # Enable CORS globally
@app.route('/api/data')
def data():
return {"message": "CORS-enabled for all origins!"}
if __name__ == '__main__':
app.run(port=5000)PHP:
<?php
header("Access-Control-Allow-Origin: *");
header("Access-Control-Allow-Methods: GET, POST, OPTIONS");
header("Access-Control-Allow-Headers: Content-Type");
echo json_encode(["message" => "CORS-enabled for all origins!"]);
?>Common CORS Errors and Troubleshooting
| Error Message | Cause | Solution |
|---|---|---|
| No ‘Access-Control-Allow-Origin’ header | Server didn’t send the CORS header. | Add the header to the server response. |
| CORS policy: Method not allowed | The HTTP method isn’t allowed. | Include the method in Access-Control-Allow-Methods. |
| Preflight request failed | OPTIONS request isn’t handled correctly. | Ensure the server responds to OPTIONS requests. |
Debugging Tips:
- Check network logs for CORS headers.
- Validate server responses.
- Test using tools like Postman (which bypass CORS for testing).
Best Practices for CORS
- Whitelist Specific Origins: Avoid using
*inAccess-Control-Allow-Originfor sensitive data. - Limit Allowed Methods: Only enable necessary HTTP methods.
- Secure Preflight Requests: Handle OPTIONS requests securely.
- Use HTTPS: Ensure secure communication channels.
- Validate Requests Server-Side: Don’t rely solely on CORS for security.
Conclusion
Understanding and implementing CORS correctly is vital for secure web application development. By managing CORS settings effectively, you can enable safe cross-origin communication while protecting your application from potential security threats.